Oct
24
2017
Sorting Algorithms Visualized
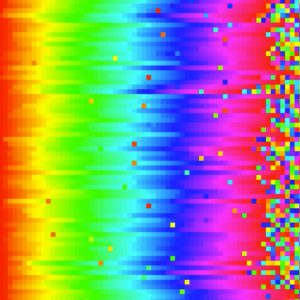
I’ve always liked sorting algorithms, so I wrote up a program to visualize them, starting with Bubble Sort. Each row of the image represents an independent list being sorted.
Source: https://imgur.com/gallery/voutF
no comments
Oct
16
2017
Key Reinstallation Attack on WPA2
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. Attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. The attack works against all modern protected Wi-Fi networks.
Quelle: KRACK Attacks: Breaking WPA2
no comments
Oct
13
2017
yes
The trivial program
yes turns out not to be so trivial after all.
Quelle: A Little Story About the `yes` Unix Command | Matthias Endler
no comments | posted in code, cool
